BTC IX: Tips to Avoid Losing Everything

In this weekly newsletter, we update you on the latest ways to do and earn more with your Bitcoin. Read more for the latest news from the Bitcoin universe and Arch community.
Roadmap
- This Week's Headlines
- One Big Thought: Tips for staying safe.
- Arch Community Updates
- Quick Hits: Watch, Read, Listen.
This Week's Headline:
💰 Brazil proposes moving up to 5% of Reserves to Bitcoin. The arms race has begun, as institutional adoption grows and nation states continue to accumulate, with Binance citing a PA News report that a National Strategic Reserve bill has passed its first committee review in Brazil.
🌎 Bitcoin family takes security global. Didi Taihuttu, the patriarch of the "Bitcoin family," is now spreading their seed phrase across four continents in light of a string of prominent kidnappings, according to CNBC.
One Big Thought:
Be safe, anon.
In the past two weeks, a number of our Bitcoin community members have been targeted — and an attack on one of us is an attack on all of us.
It started with our own Chief Marketing Officer, Nick Four, being targeted after the Bitcoin summit, leading to five-digits worth of crypto assets being stolen and his personal email being commandeered for days.
Then both Jan Smejkal, Chief Strategy Officer at XVerse, and our friend and ambassador Melina (@Girl_intheVerse) had their X accounts compromised by social engineering scams.
These are smart, high-level Bitcoiners who had 2fa and other precautions set up to try to prevent things like this — a reminder that even the most prepared and experienced of us can sometimes fall prey.
Here are some reminders on best practices:
#1 Be very careful about the links you click, particularly those that don't come directly from an in-app notification
In both Jan and Melina's cases, the scammers tricked them by sending emails that looked like they had come from X.
When you click on links within the email, it will ask you to log in to a site that looks very similar to X — and when you do, the hackers will have your username and password, and quickly lock you out of your own account.
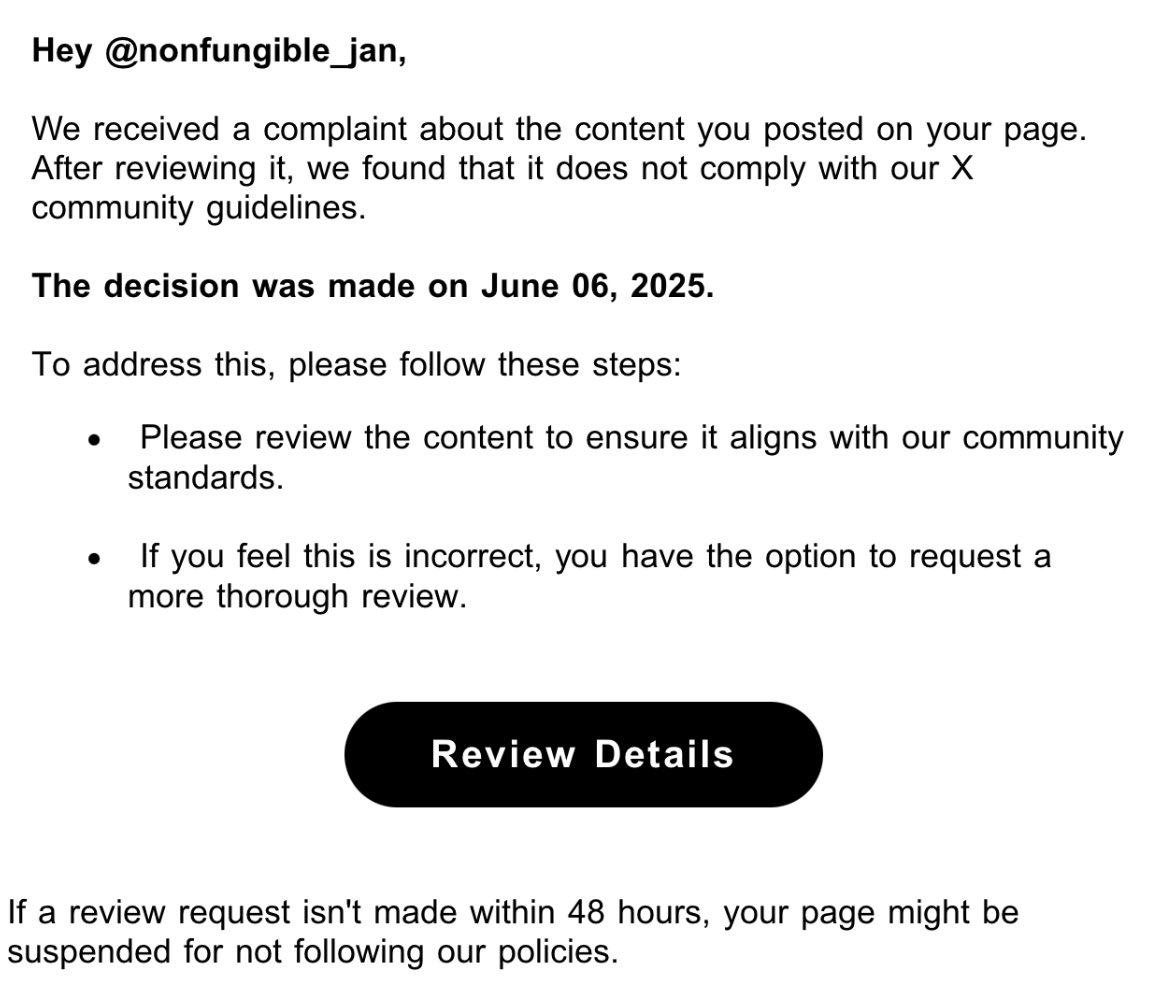
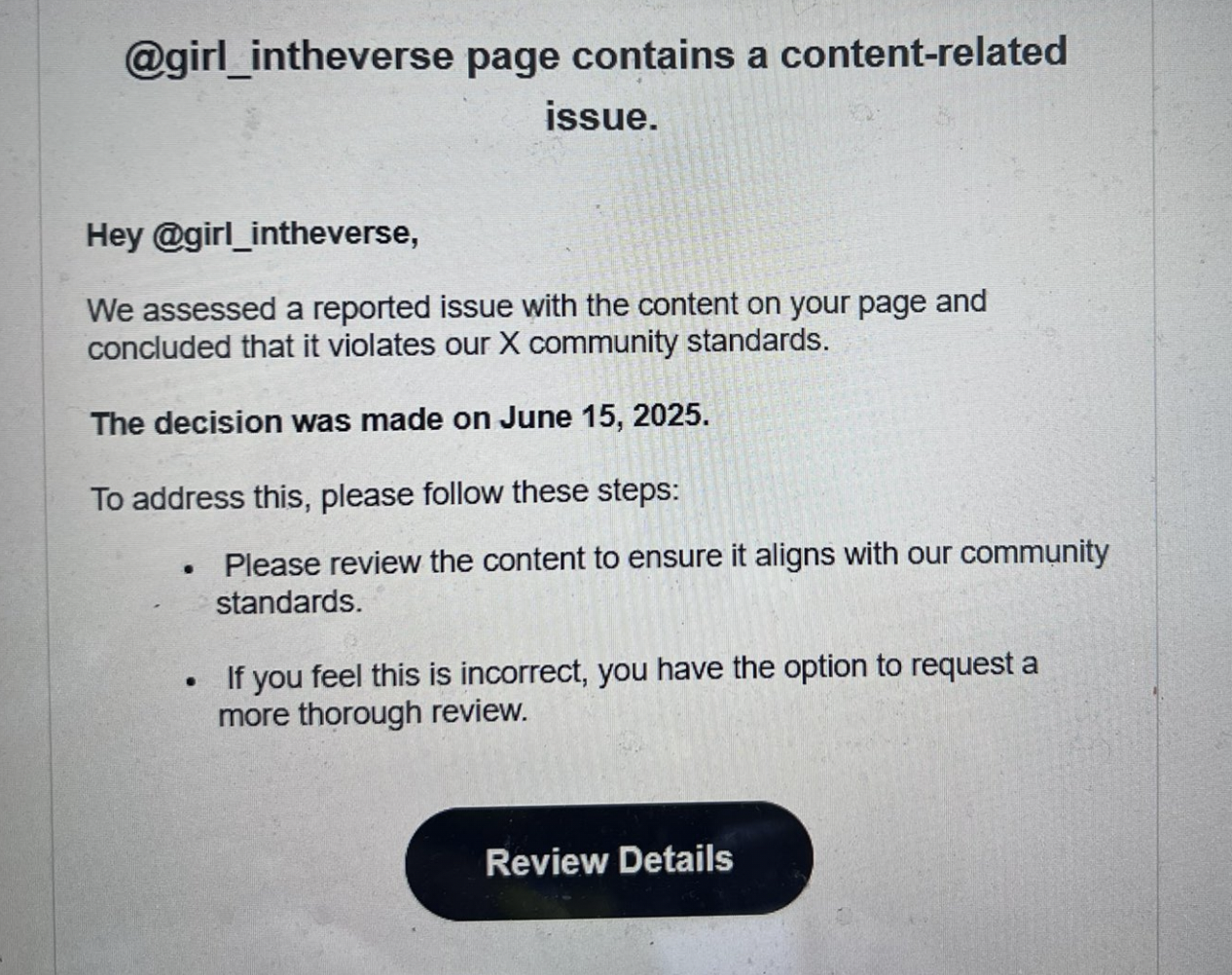
To spot fake X (formerly Twitter) login emails and protect your account from hackers ...
1) Aways check the sender's email address carefully—official X emails come from domains like @twitter.com, not suspicious or misspelled variations.
2) Be wary of urgent language or scare tactics, like claims that your account will be suspended unless you click a link.
3) Avoid clicking on links directly from emails; instead, go to the official X website or app to verify any alerts.
4) Look for grammar or formatting errors, which are common in phishing attempts.
5) Finally, enable two-factor authentication (2FA) to add an extra layer of security in case your login credentials are ever compromised.
#2 If somebody asks you to download new software to do a video call, it's almost certainly a scam
Our CMO, Nick Four, gets asked to go on dozens of podcasts, and often agrees to do so to both spread the news of Bitcoin/Arch and to help people grow their own followings.
Two weeks before our major event at BTC Vegas, an X personality with 10K followers and a history of seemingly normal content reached out asking to do one of those podcasts.
He seemed genuine, explaining the purpose of the podcast, its history, and its affiliation with a noteworthy VC firm. He even jumped on multiple calls to discuss the contents of the podcast, and sent questions ahead of time.
Nick finally agreed on a time for the podcast while on vacation shortly after BTC Vegas.
It had been a long week, with a lot of exciting moments. But it was also extremely busy — and so he was pretty beat when he hopped on the Google Meet.
The podcaster told him that he would need to download audio software similar to StreamYard to be interviewed by the other hosts, who he said were based in China and, thus, couldn't use Meet.
He had a feeling that something was sketchy, but decided to do it anyway, not wanting to disappoint the guy.
The download looked like a real conferencing platform, but ended up being "OS_AtomStealer" — a known malware that ended up draining his hot wallets, stealing his login information to his personal email, and other data stored on his Chrome profile.
He was eventually able to get his gmail back with the help of a relative who works at Google, and was able to freeze some stolen USDC with the help of a security team ... but many of his losses were irretrievable.
Here are some tips to avoid falling victim to scams like this:
- Trust your instincts—hesitation is a signal. If something feels off, don’t ignore it. Legitimate opportunities can wait; scammers rely on urgency and politeness to bypass your gut feeling.
- Never download unfamiliar software at someone else’s request. Reputable podcasts and media outlets will use widely known tools like Zoom, Riverside, or StreamYard. If someone insists on a custom or obscure platform, treat it as a red flag.
- Verify identities and affiliations independently. Just because someone has followers and polished messaging doesn’t make them legit. Contact the VC firm, podcast hosts, or organizations they claim to be affiliated with via official channels—not links they provide.
- Use a separate device or “clean” environment for interviews. If you do agree to calls with less-known individuals, avoid doing them on devices with sensitive data or connected crypto wallets.
- Secure your digital presence. Use hardware wallets for crypto, enable 2FA on all important accounts, and avoid storing passwords or sensitive info in your browser profile.
- Always ask: What do I stand to lose if this is fake? Especially when you're tired, traveling, or in a busy period, take extra precautions before clicking or downloading anything.
These scams are becoming more sophisticated, often blending technical trickery with social engineering. Staying skeptical—even when someone seems friendly or credible—isn’t rude. It’s smart.
#3 Make sure your tech stack is as secure as possible
🔐 Account Security
- Enable Two-Factor Authentication (2FA)
Use app-based 2FA (like Authy, Google Authenticator) or physical security keys (like YubiKey) instead of SMS, which is vulnerable to SIM swaps. - Use Strong, Unique Passwords
Create complex passwords and never reuse them across services. Use a reputable password manager (like 1Password or Bitwarden) to store them securely. - Use Passkeys Where Supported
Passkeys are phishing-resistant alternatives to passwords and are supported by Apple, Google, and many major platforms. - Consider going "email only" for 2FA
Remove your phone number so hackers can't use a sim swap to access your accounts.
🛡️ Device & Browser Security
- Keep Software and OS Up to Date
Always install updates for your OS, browser, and apps. Many updates patch known security vulnerabilities. - Avoid Browser Auto-Save for Passwords
Use a password manager instead of saving passwords directly in your browser, which can be compromised. - Use Secure Browsers and Extensions
Use privacy-focused browsers (like Brave or Firefox) and install extensions like uBlock Origin or HTTPS Everywhere for safer browsing.
🧱 Hardware & Physical Security
- Use a Hardware Wallet for Crypto
Store digital assets in a hardware wallet (e.g. Ledger, Trezor) to keep private keys offline. - Use a Hardware Security Key
Devices like YubiKey or Google Titan Key provide physical authentication for your logins. - Have a Separate “Clean” Device
Keep a secondary device for sensitive tasks (e.g. managing wallets, admin accounts) that is never used for downloads or general browsing.
Hopefully you can avoid being a victim to these types of scams or hacks in the future — and if you are part of the Arch community and do have any issues, don't hesitate to reach out. We will help if we can.
Arch Updates:
Product Updates:
✅ File-Based Database Architecture for Scalable Performance
Replaced legacy database storage with a high-performance file-based indexing system. Account lookups and transaction history retrieval are now faster and more scalable, enabling financial-grade throughput and reliability for DeFi and enterprise applications.
✅ Bulletproof Synchronization System
Introduced robust rollback and reapplication mechanisms for seamless state recovery during Bitcoin chain reorganizations or validator disconnections. Ensures validators stay in sync with no manual intervention — a critical feature for high-availability systems.
✅ Memory Optimization in Execution Pathways
Implemented smart memory management by eliminating unnecessary heap allocations in core system calls. Enables higher throughput and stability under load while reducing validator resource consumption.
✅ CLI Developer Tools Overhaul
Redesigned the CLI for frictionless deployment and testing. Developers can now spin up validator networks and containerized environments with a single command. The new tooling dramatically improves testnet workflows and lowers barriers to entry.
Join 104K+ Bitcoin builders in the Arch Discord
Quick Hits:
📺 Watch
"What sets Arch apart is that we have already built and shipped a full featured execution layer with a custom VM specifically designed for Bitcoin architecture."
— Arch Network (@ArchNtwrk) June 1, 2025
🎙️Arch CEO @proofofmud on how Arch is different from other programmability options on Bitcoin.
Thanks to… pic.twitter.com/kIrSfrwoAX
📖 Read
- The Problems Every BTC Dev Faces — And How the ArchVM Tackles Them
- How Cross-Program Invocation Unlocks BTC Composability
🎧 Listen
The True Story of Bitcoin Pizza Day https://t.co/1LxDepkxNN
— cbspears ◉ (@cbspears) May 25, 2025

